I would like to enable OTA firmware updates by flashing them from the bootloader to the application flash. This works without issue when read protection is disabled, but it fails with read protection enabled. I found a relevant section in the datasheet. Is there absolutely no way to flash the first 4KB of application flash from the bootloader while read protection is active?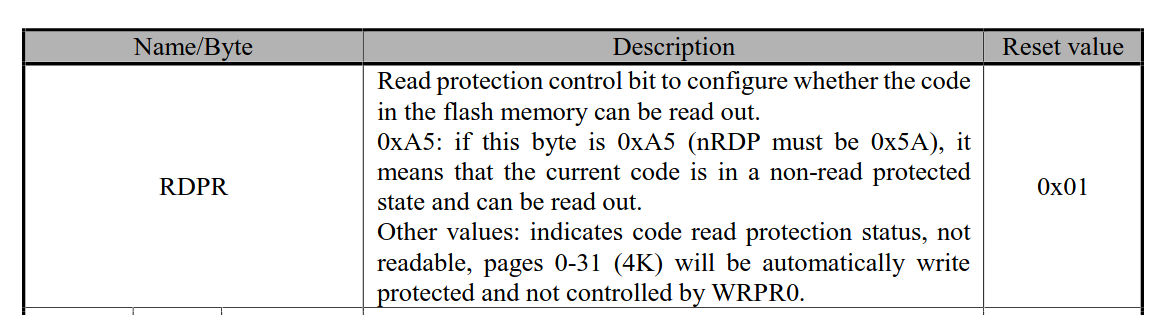
Hello, after enabling read protection, it is not possible to perform write operations on this area. It is recommended that you add a read protection removal operation in the bootloader program. After the read protection is removed, perform IAP upgrade write operations. After the IAP upgrade is completed, enable read protection again.
Thank you for the response! Do you have any ideas on how to preserve user data when disabling read protection? The user data section is the last 1KB of flash. Additionally, how can I securely handle encryption keys if read protection needs to be disabled during updates?
I have a solution that works for now but i think it's not great. Before disabling read protection, I load the 1KB of user data into RAM. After disabling read protection and performing a reset, I reuse the existing RAM allocation and load the data section back. I then execute the update and re-enable read protection. Is this a safe approach, or is there a high risk of the RAM containing faulty data becasue of the reset?
Hello, the data in RAM may be lost after power on or reset, and this method is not as reliable. If you want to upgrade IAP, there is a routine for upgrading IAP through serial port in CH32V003 EVT. It is recommended that you refer to it. The EVT download link is as follows. If there are any issues in the future, please email us( lzs@wch.cn )Communication.
/downloads/CH32V003EVT_ZIP.html
I'm still encountering the same issue and haven't been able to find a solution. Is there no reliable method to restore app flash data after disabling read protection? The 64 bytes section after the User option bytes is to little. If the answer is no, would it pose a security risk to save an encryption key in the 64 bytes User option bytes?, given that it's not read-protected.
